Automagically Restarting Web and Function Apps
There certainly is a lot of talk in Azure about how to automatically do certain activities like restarting an application when an error threshold has been exceeded. However, there isn’t much material readily available stepping through the configuration of this, even less if you want to involve Managed Identities.
Let’s look at this scenario and walkthrough how to create something that will auto restart your application. This will focus on the actual restart process as the trigger can be anything. I’ll mention how setup and queue the trigger, it’ll be up to you to configure when to execute it.
There are multiple solutions on how to restart a web application within Azure. One could use PowerShell with an Automation account, a custom function hitting a REST endpoint or a Logic App. For simplicity we will focus on using a Logic App.
Logic Apps
Azure Logic Apps is a code free integration tool billed at a per execution-based billing model. One of its biggest selling points is all the Logic App Connectors available to enable integration and orchestration across products. For this purpose, we just need to have an HTTP trigger that will call the Web Apps Restart endpoint. Seems straightforward and it surprisingly is.
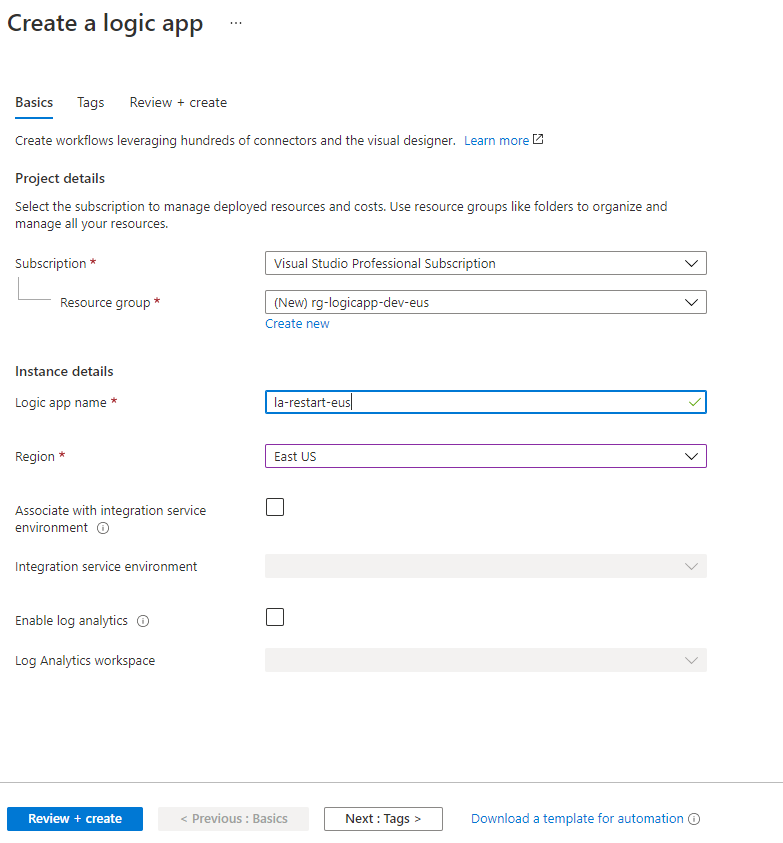
Create the logic app in a similar screen as:
Select Blank App to start with a new canvas.
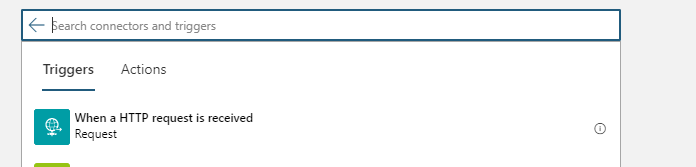
The first thing that needs to be defined is what will be the trigger to the Logic App. For this search for HTTP and select request:
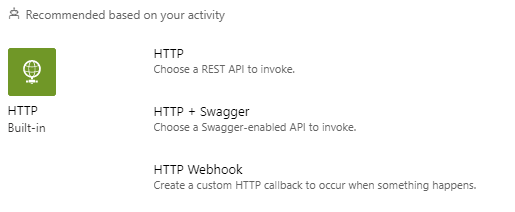
After this select the “+ new step” button as we will want to then call our REST API endpoint to restart the web app.
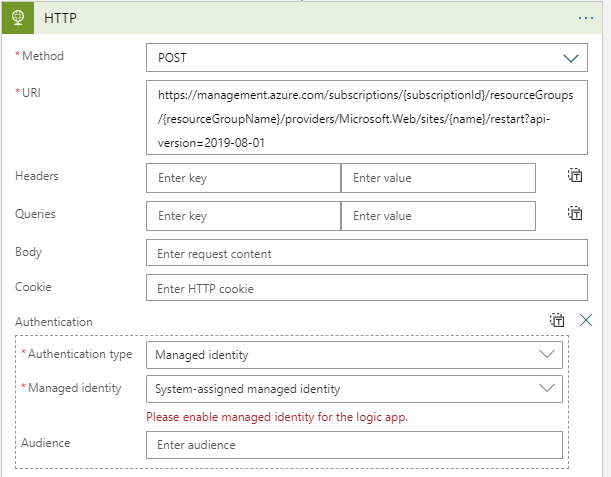
For Method select POST and insert this into the URI: https://management.azure.com/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.Web/sites/{name}/restart?api-version=2019-08-01 be sure to update the URL with your subscriptionId, resourceGroupName, and app name.
Select ‘Add new parameter’ ->Authentication. From here we want to tell the REST API endpoint that we will be authenticating as the Logic App itself. Now if the Logic App hasn’t been configured for Managed Identity a soft warning will appear like:
To turn this feature on navigate to the Logic App -> Settings-> Identity and turn the Status to On:
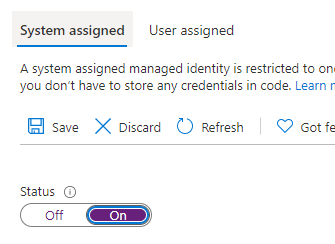
If unfamiliar this is registering the Logic App as an identity in your tenant’s Azure Active Directory. This will allow the Logic App to be authenticated and set up permissions for it as well.
This leads to the next step. The Logic App has been created; however, it does not have the authorization to restart the web app. To achieve this navigate to the Subscription->Select correct one -> Access control(IAM) -> Search for WebsiteContributor: (note this is done at subscription assuming you may want to pass in the website as a parameter and as such want the logic app to inherit access across all sites)
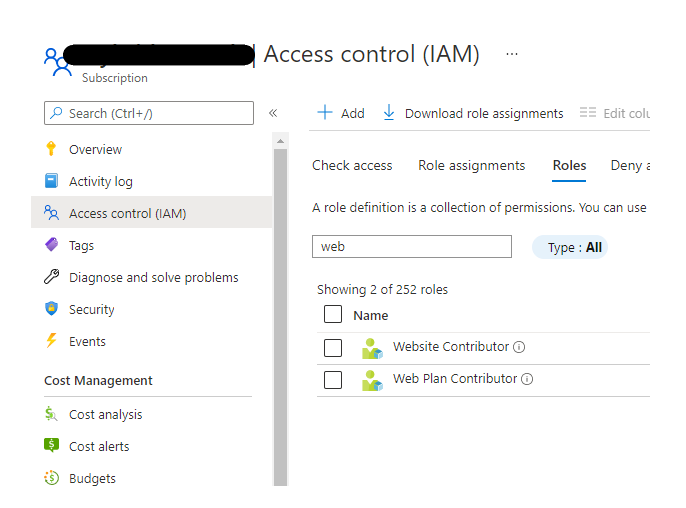
Next select + Add role assignment and select the Logic App.
Let’s test out the Logic App now. Navigate to it and select Run Trigger. We should see:
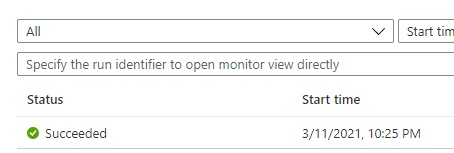
But how to confirm this actually worked? One such way is to check the Activity Log of the Web App. Once access this we can see that a Restart was initiated by the Logic App:
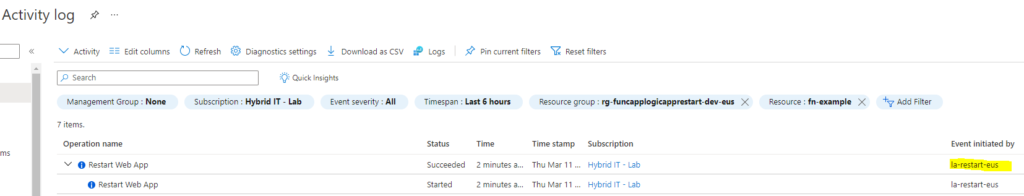
Great! So now how to get this logic app to automatically be triggered? Well Logic App is one of the events that can be triggered via an Azure Action Group Once it’s configured as an Acton Group it can be triggered by any number of Conditions.
Future Considerations
Logic Apps can be a great code free way to quickly put something together. However; as with anything well implemented in Azure an engineer should consider how to deploy these types of resources as IaC. Logic Apps work great with ARM deployments as can quickly view code and see how to deploy this.
Terraform is a little different. There are logic app resources; however, at the time of this article there is an open request to add the ability to create Managed Identities.
Discover more from John Folberth
Subscribe to get the latest posts sent to your email.
Thank you for this useful tip.
Hi,
I am getting an issue where it is telling me to enter a valid url. Any tips?
Thanks!
Sorry for late response. I will need to take a look as it’s been a little while.