Managed Identities for Azure Automation Accounts
Something that was recently announced by Microsoft is the ability to have Azure Automation Accounts be configured to use Managed Identities.
Code
This is a big step in driving adoption of Managed Identities. Previously one would have had to configure the Azure Automation Account to execute as a Run As Account. This Run As Account relies on credentials which have an expiration date. In addition, the previous script was required to have the Automation Account essentially log in to Azure via Azure PowerShell.
$logonAttempt = 0
while(!($connectionResult) -and ($logonAttempt -le 10))
{
try{
$LogonAttempt++
# Logging in to Azure...
$connectionResult = Connect-AzAccount `
-ServicePrincipal `
-Tenant $connection.TenantID `
-ApplicationId $connection.ApplicationID `
-CertificateThumbprint $connection.CertificateThumbprint
Start-Sleep -Seconds 30
Write-Output 'Connected to Azure'
}
catch {
Write-Output 'Unable to connect to Azure'
}
}Ugly as essentially, we are having to manually log in with our Automation Account. With the introduction of support for Managed Identities all of this code can be replaced with in essence one line:
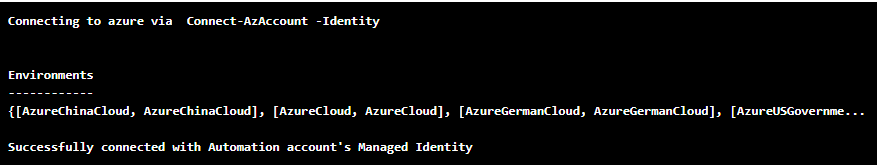
Write-Output "Connecting to azure via Connect-AzAccount -Identity"
Connect-AzAccount -Identity
Write-Output "Successfully connected with Automation account's Managed Identity" Now the Automation Account can authenticate to Azure as itself without needed to exchange any credentials. Here is the log to prove successful connectivity:
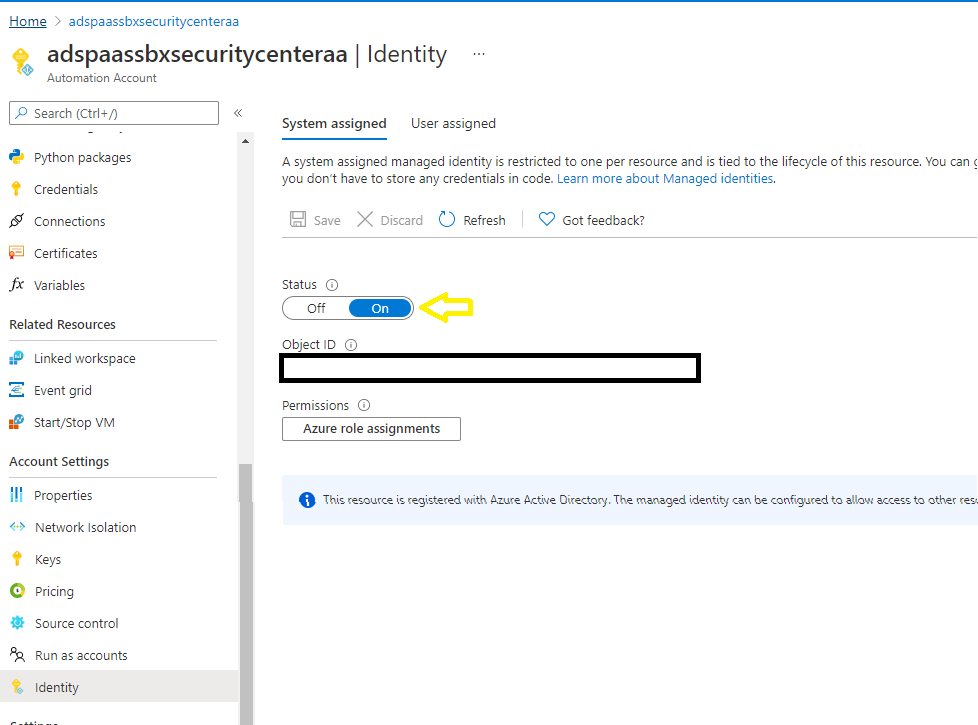
The best part is to switch over is very, very, easy. One just needs to enable the System Identity via the portal or ARM/bicep (Terraform does not support this yet). Here is how for the portal via Account Settings->Identity
Via Bicep/ARM
identity: {
type: 'SystemAssigned'
}Next Steps
If wanting to know how to have these modules auto update check out my post outlining how to do this.
Conclusion
With Microsoft moving more and more to leveraging Managed Identifies as its preferred method for Azure Resource authentication it would be beneficial for users to incorporate this more and more into their solutions. The migration path is easy and fundamentally it is more secure since there is no exchange of credentials.
Discover more from John Folberth
Subscribe to get the latest posts sent to your email.